Microsoft SentinelFormerly Azure Sentinel
Overview
What is Microsoft Sentinel?
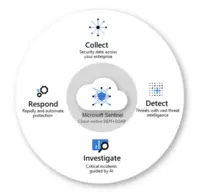
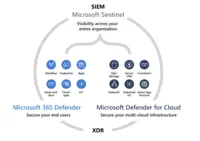
Microsoft Sentinel (formerly Azure Sentinel) is designed as a birds-eye view across the enterprise. It is presented as a security information and event management (SIEM) solution for proactive threat detection, investigation, and response.
SIEM means Sentinel
Why you should start using Microsoft Sentinel today.
Sentinel: Your one stop SIEM for cloud for Bird's Eyes by MS.
Microsoft Sentinel, the scaleable cloud-native SIEM platform
Unleashing the Power of Data for Seamless Security Investigations
Review of Microsoft Sentinel
One stop solution for all security needs. Transforming Security with AI and Automation
Excellent cloud security solution with intelligent analytics and automation offered by Microsoft.
A big SIEM or a little SOAR?
Microsoft Sentinel Review
Microsoft Sentinel Review
Microsoft Sentinel Review
Microsoft Sentinel Review
Microsoft Sentinel
How Microsoft Sentinel Differs From Its Competitors
Sources
Third party products include Workday, Google Workspaces, …
AI and ML
While I have a very limited experience with using Azure Open AI in the incident through playbooks, it surely …
Investigation Tools
Sources
Investigation Tools
Sources
On-Premises Identity events
Azure platform events
Defender and other Microsoft products
On-premises appliances
Linux events
This same counts towards Azure activity, Azure VMs and …
AI and ML
Next to that we use the Fusion rules that will detect multi-stage attack scenarios
Sentinel notebooks are not used a lot at this moment, because of the learning curve
Investigation Tools
Sources
AI and ML
Investigation Tools
Investigation Tools
Sources
AI and ML
Investigation Tools
Sources
Investigation Tools
Sources
AI and ML
Investigation Tools
Sources
AI and ML
Investigation Tools
Awards
Products that are considered exceptional by their customers based on a variety of criteria win TrustRadius awards. Learn more about the types of TrustRadius awards to make the best purchase decision. More about TrustRadius Awards
Popular Features
- Centralized event and log data collection (14)8.686%
- Correlation (14)8.484%
- Event and log normalization/management (14)8.282%
- Custom dashboards and workspaces (14)7.474%
Reviewer Pros & Cons
- Sentinel is by far the most efficient tool in supporting the highest number of solutions and products when it comes to data connection (or ingestion) ...
- 'Notebook' has always been a very hard to use feature for me in Sentinel. From my experience, there have been a very selective use cases for this feat...
Pricing
Azure Sentinel
$2.46
100 GB per day
$123.00
200 GB per day
$221.40
Entry-level set up fee?
- No setup fee
Offerings
- Free Trial
- Free/Freemium Version
- Premium Consulting/Integration Services
Product Demos
Microsoft Sentinel: Monitoring health and integrity of analytics rules
Features
Security Information and Event Management (SIEM)
Security Information and Event Management is a category of security software that allows security analysts to look at a more comprehensive view of security logs and events than would be possible by looking at the log files of individual, point security tools
- 8.6Centralized event and log data collection(14) Ratings
Effectiveness of real-time centralized event and log data collection
- 8.4Correlation(14) Ratings
Correlation of logs and events to pinpoint significant threats
- 8.2Event and log normalization/management(14) Ratings
Ability to normalize event syntax so that logs can be compared and are machine-understandable
- 9.2Deployment flexibility(13) Ratings
Ability to tune system to maximize threat detection and minimize false positives
- 8.5Integration with Identity and Access Management Tools(13) Ratings
Integration with access control tools like Active Directory and LDAP
- 7.4Custom dashboards and workspaces(14) Ratings
dashboards that can be customized to meet the needs of specific groups
- 7.6Host and network-based intrusion detection(13) Ratings
Ability to detect both endpoint intrusion and network ingress detection
- 8.2Data integration/API management(14) Ratings
Ease and quality of data integrations between SIEM and other systems
- 8.7Behavioral analytics and baselining(12) Ratings
How effectively activity and behavior baselines are established and maintained
- 8.5Rules-based and algorithmic detection thresholds(13) Ratings
Effectiveness of manually-established rules and algorithmically-determined detection thresholds
- 8.4Response orchestration and automation(14) Ratings
Quality of built-in response orchestration and automation in Next-Gen SIEM
- 9Reporting and compliance management(4) Ratings
Ease and quality of reporting and compliance functions
- 8.6Incident indexing/searching(14) Ratings
Effectiveness of searching across structured and unstructured events and incidents within SIEM
Product Details
- About
- Competitors
- Tech Details
- FAQs
What is Microsoft Sentinel?
Helps users to protect the digital estate: Secures the digital estate with scalable, integrated coverage for a hybrid, multicloud, multiplatform business.
Microsoft intelligence to Empower SOC: Optimizes SecOps with advanced AI, security expertise, and threat intelligence.
Detection, investigation and Response: A unified set of tools to monitor, manage, and respond to incidents.
Cost of ownership: A cloud-native SaaS solution to reduce infrastructural costs.
Microsoft Sentinel Features
Security Information and Event Management (SIEM) Features
- Supported: Centralized event and log data collection
- Supported: Correlation
- Supported: Event and log normalization/management
- Supported: Deployment flexibility
- Supported: Integration with Identity and Access Management Tools
- Supported: Custom dashboards and workspaces
- Supported: Host and network-based intrusion detection
- Supported: Log retention
- Supported: Data integration/API management
- Supported: Behavioral analytics and baselining
- Supported: Rules-based and algorithmic detection thresholds
- Supported: Response orchestration and automation
- Supported: Incident indexing/searching
Microsoft Sentinel Screenshots
Microsoft Sentinel Videos
Microsoft Sentinel Competitors
Microsoft Sentinel Technical Details
| Deployment Types | Software as a Service (SaaS), Cloud, or Web-Based |
|---|---|
| Operating Systems | Unspecified |
| Mobile Application | No |
Frequently Asked Questions
Comparisons
Compare with
Reviews and Ratings
(66)Attribute Ratings
Reviews
(1-11 of 11)SIEM means Sentinel
- Sentinel is by far the most efficient tool in supporting the highest number of solutions and products when it comes to data connection (or ingestion) and that too in the least complex manner possible. Most of the data connectors in Sentinel are very easy to configure and deploy.
- Incident Management is undoubtedly one of the main USPs of Sentinel. With an easy-to-use UI, variety of utilities (adding tasks, manual triggering of playbooks, activity logs etc.) and provision of having an investigation map from the incident details page, Sentinel clearly stands out in this area.
- I personally love the feature of integrating 'Threat Intelligence' to Sentinel from a free and one of the most reliable sources, Microsoft itself. This not only saves time for an analyst in checking the reputation of an entity but also allows to take actions on the suspicious entities at earliest.
- 'Notebook' has always been a very hard to use feature for me in Sentinel. From my experience, there have been a very selective use cases for this feature across the industry.
- 'Entity Behavior' has some scope to be improved further since it is a feature that gives some useful insights but needs to be accessed separately. I think it should be re-worked in a way to be used within the incident investigation page.
- I'd like to see a more user-friendly version of the 'Content Hub' menu which was the earlier version! The new UI is somewhat confusing to use and is dependent on a lot of filters being applied which do not even lasts for a single session. With each refresh, we have to apply the filters again.
Sentinel is a very good tool for log analysis and event management purposes as well. With KQL and ASIM parsers, organizations can retrieve invaluable insights even from the most complex data.
And of course, Sentinel is a great choice for automating the incident response process to a very good extent.
Why you should start using Microsoft Sentinel today.
- Correlating Security Data.
- Automated response.
- Threat Intelligence mapping.
- Performance on data ingestion.
- Performance on query data.
- Normalizing data.
Microsoft Sentinel, the scaleable cloud-native SIEM platform
- It has a native integration with all Microsoft products, from Entra to Azure, Microsoft 365
- Being built upon native Azure functionality benefits in automation and infrastructual solutions
- The KQL language is relatively easy to learn and powerful.
- Microsoft is listening very careful to the customers and develops new functionality at a fast pace
- The solution can become very expensive when not used in an effective way
- The SOAR functionality can be more powerful compared to other products
- Ingestions delays are not often clear and have to be taken care of thoroughly
When companies have no Microsoft footprint it still can be an excellent product, but it lacks integration and UEBA/Fusion have none or less additional value.
Compared with other SIEM solutions it is a very good product, but keep in mind that using Microsoft products will get you on the right track out of the box
Review of Microsoft Sentinel
- Threat Detection and faster Analysis
- Security Automation and architecture improvement
- Onboarding and integration with client/our system can be simplified so that it can be used by everyone.
- Integration takes longer if software is hosted outside.
- The logs of softwares hosted in-house has room for improvement
Excellent cloud security solution with intelligent analytics and automation offered by Microsoft.
- It interacts easily with Azure, Active Directory, and log analytics, and it can route data via Sentinel as well as establish alerts and other workflows to respond to possible security concerns.
- It features a highly user-friendly UI that makes it simple to operate the platform, and the kql is simple to use while studying logs.
- It is one of the greatest platforms for totally cloud deployment, which improves productivity. It can evaluate vast amounts of data quickly and is incredibly productive.
- It takes some time to learn how to use and install it properly, and it does not connect effectively with external PaaS systems such as Salesforce CRM, Salesforce Commerce Cloud, and so on.
- Microsoft can simplify the display of the logs to make them easier to study, and the user interface occasionally delays, which can also be enhanced.
A big SIEM or a little SOAR?
- KQL Query language is easy to learn and very powerful once mastered.
- A continuously growing list of connectors allows the integration of hundreds of technologies.
- Microsoft Sentinel provides the best integrations with Microsoft's products.
- Like many Microsoft products, the solution can lose its effectiveness in non-Microsoft environments.
- It's not the most cost-effective solution out there.
- False positives are something that really needs to be addressed when confronting Microsoft Sentinel.
Microsoft Sentinel Review
- It's good in form of the integration with the Microsoft native products like Defender or Office 365 and some of the queue, the complete visibility because if we are using the Microsoft product suite as the operating system on the endpoint and the Microsoft Defender and those things, so its is a complete end to end visibility, not just for as a sim but complete visibility of our identity. We are also having Azure ready. It gives more visibility, the users, the endpoint, and my SaaS services like the teams or I can say Outlook. I get a good visibility and the next good thing is I can mitigate the threat in real time. I can write the playbook and I can do the hunting. One of the good things Defender, I see the hunting in the playbooks. So my form analyst where from one place where I could do the monitoring, triage response, and mitigation.
- Some of the integration though it provides integration to most of the technologies, but I still think it is a scope of integration, scope for implementing the integration area so that I can integrate all the design sources to the central. Right now I experienced some challenges with my team with that.
Microsoft Sentinel Review
- It really does do a very good job of collecting end user data or end user and device data to correlate against.
- Their UEBA really needs to grow out of the Microsoft space.
- I think they need to be a little bit more friendly using their workbooks, so that's probably where I see it should grow.
Microsoft Sentinel Review
- It handles a lot of data. It works fast, it's easy to understand. It's the integrations with all the products, the APIs defender with Office 365 with Azure ad. It's got some great integrations.
- I think that the handling of ingestion delays and time generated, I think that's currently the main issue because you get some data that comes in later, and some data comes way later, so you have to correlate it and it can be a bit of a hassle to make sure to align the right data with each other.
- Advanced analytics and machine learning algorithms
- Easy to deploy, manage, and update
- Huge list of out-of-the-box dashboards, reports and automation playbooks
- Query language is quite difficult
- Automation playbooks some times have false positives alerts/responses
1. Network-based intrusion detection - monitoring security events on the company Edge environment (firewalls, VPN gateways) - this is easy to do with built-in content hubs that provide sets of analytics rules (unfortunately, not always), dashboards, and automation playbooks for almost all vendors
2. Host-based intrusion detection - end users desktops monitoring - here we use integration with cloud MS Defender deployment that provides all information from agents on local machines.
- Easy to deploy and learn to use.
- Artificial intelligence.
- Analysis of any type of threat, including those that have not yet been discovered.
- Automation to respond to security incidents.
- Reduction of false positives.
- Easy to edit log analysis rules.
- The reporting feature can be improved. I sometimes see problems with exportation, instability and compatibility.
- Dependence on Microsoft Azure software.